If you have been following the news in recent years, you would agree that cybersecurity threats are getting increasingly complex. Aside from their complexity, their numbers are on the rise, too. These threats not only affect small-to-midsize organizations but even large ones that proactively take measures to secure their networks in an effort to stay ahead of the curve.
It would be interesting to talk about how security breaches occur. However, for now, I would like to share my thoughts on what solution an enterprise can use to mitigate the risk of such attacks so that hackers are kept at bay. Once their networks are secure, businesses can then do what they do best, which is to improve their internal processes, better serve their customers and stakeholders, and grow the business further.
While there are quite a few security solutions in the market, a popular option available is a security information and event management (SIEM) system. It is extremely versatile and, in my opinion, better serves organizations with complex business processes and systems using a holistic approach.
In a nutshell, here is how it works:
- It proactively logs and analyzes data pertaining to every activity on corporate networks in an attempt to detect irregularities.
- According to the Cyber Security Survey Report1, it takes 175 days on average to detect an attack. The SIEM system can be set to analyze log records with great speed and dramatically reduce detection time.
- An SIEM system has the capability to monitor the networks and detect attacks or potential attacks in real-time.
- Once it detects an event, it can assess if the threat is real or a false positive. If the threat is real, it executes pre-configured workflows to eliminate it.
- It can identify threat sources from trusted third-party open-source feeds and suspicious incidents caused by these sources. Once it has this information, it can search the organizational networks to assess the presence of any abnormalities.
- The SIEM system employs artificial intelligence and machine learning techniques to learn from user behaviour over time as they interact with systems. For example it can learn the time when a specific user usually logs on to a particular system, collect information on and report any anomalous / suspicious activity.
All the above methodologies combined, make the SIEM a robust system that can put the proactive / worrier IT managers at ease. However, as good as an SIEM system is, there is still the concern of how soon can the concerned IT personnel or workgroups know if a potential or actual threat is detected, or a system anomaly occurs, or any network irregularities are discovered.
That is where a notification management platform (NMP) like sendQuick comes into the picture that would seamlessly integrate with an SIEM system since the main goal of implementing this system is to reduce the mean time to know (MTTK) and update the IT personnel as soon as a user-specified event or threat is detected.
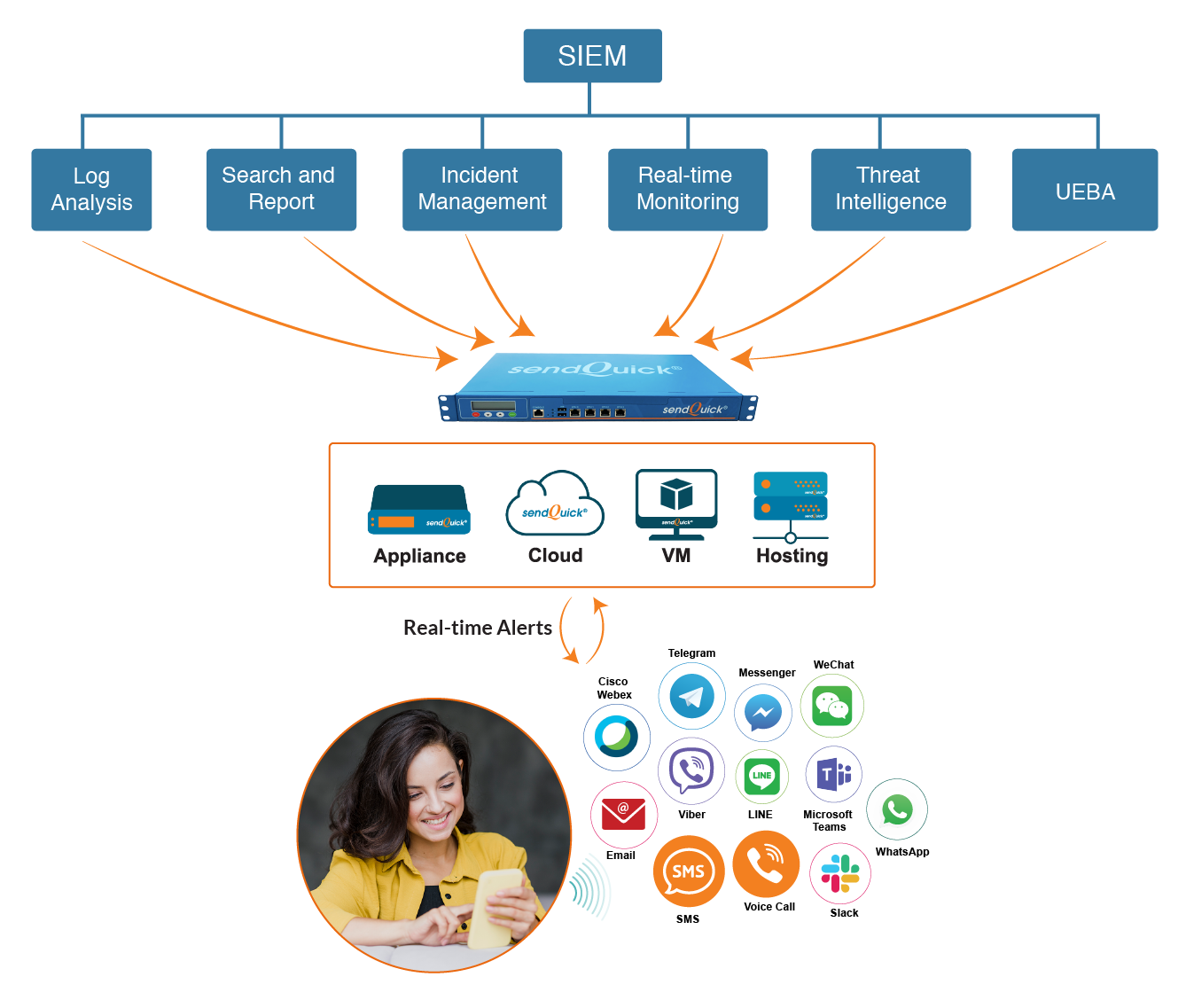
A good NMP should have the following features to function at scale:
Omnichannel Alerts
Any time an SIEM system detects any unusual activity, it would send a notification email to an NMP which then will convert it into SMS, automated voice calls, social messenger app (like Facebook Messenger, WhatsApp, WeChat, Viber, LINE, Telegram), and team collaboration tool (including Cisco Webex, Microsoft Teams and Slack) messages before sending them to authorized IT personnel..
User Management and Preference
The NMP should be able to support an unlimited number of users. The traditional way of transmitting alerts has been using SMS or text messages. However, for one reason or another, an IT manager may prefer to receive notifications in formats other than SMS (or text messages). The NMP should have a provision to send alerts to the user’s desired communication channels.
Escalation Management
Let’s think of a scenario where the SIEM sends an incident alert to an NMP to distribute to an IT workgroup or a single user. The recipient/s is/are required to acknowledge the receipt of incoming alerts. But what if they do not? In such a case, the alerts should be escalated to another user-specified IT workgroup or individual so that a speedy remediation of the incident can occur.
Roster Management
Not all alerts should be forwarded to all IT managers, and, for this reason, incident alerts should only be sent to personnel on duty at the time the incident is detected so they can address it accordingly. An NMP should have a built-in list of personnel and the days and hours during which they are on duty.
Message Filtering
The IT managers should not be inundated with alerts, but, rather, be sent only the relevant ones to help them avoid alert fatigue. Therefore, an NMP should be able to filter alerts for relevant keywords and forward the same to them.
Uptime and Maintenance
The NMP should have a high availability (HA) option so it can deliver 100% uptime and needs to be maintenance free so then its total cost of ownership (TCO) will be low.
About sendQuick
IT Notification Management for Enterprises
Designed and developed with passionate rigor, the purpose of the sendQuick IT notification management platform is to deliver real-time notification management workflows 365 days a year. It is a high scalable plug & play solution and seamlessly integrates with any SIEM system to notify on any anomalous behaviour or indicator of compromise (IoC) for efficiently functioning corporate networks.
Click the Request for Information button, below, and get in touch with us should you need further clarification and we will be happy to assist you.






